If you are a penetration tester, there are several tools that can greatly assist you in your work. In this article, we will discuss ten essential tools that every cybersecurity enthusiast should be familiar with. These tools cover a range of functionalities, from scanning to post-exploitation techniques. By understanding and utilizing these tools effectively, you can enhance your cybersecurity skills and perform comprehensive assessments and tests.
Wireshark

Having a strong foundation in networking is crucial for becoming a competent pentester.
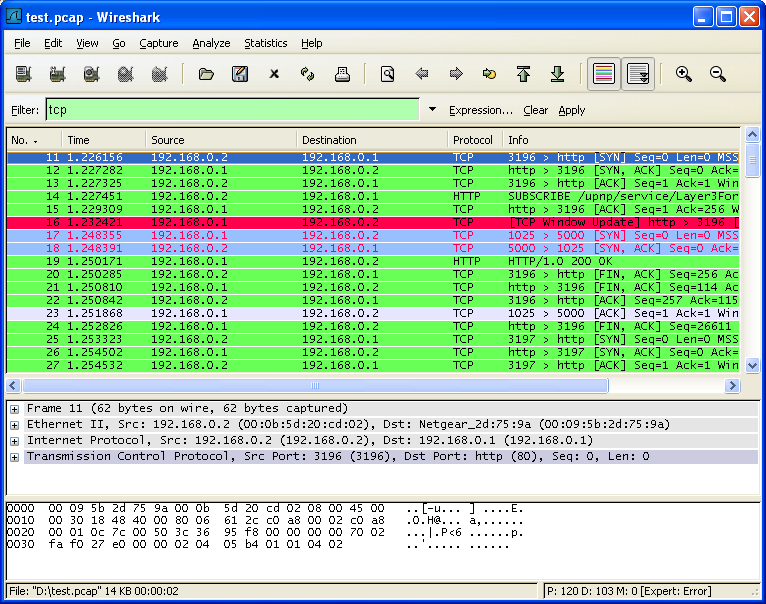
Wireshark is the best tool for network analysis. This open-source tool allows you to analyze network logs in real-time. Wireshark can dissect data packets into frames and segments, providing detailed information about the bits and bytes within a packet. By using Wireshark, you can examine network traffic, identify potential vulnerabilities, and gain insights into the communication between different network devices. Its powerful features make it an essential tool for any cybersecurity professional.
Nmap

scanning tool is incredibly helpful during the footprinting process of a targeted network. It provides information such as open ports, services, and the operating system running on the target computer.
For basic scanning, many professionals are transitioning to using naabu as it is built using the Go language, resulting in faster performance. However, in terms of features, Nmap remains more comprehensive compared to similar tools. Therefore, Nmap continues to be the best tool in the network scanning category.
Nmap also offers a GUI version called Zenmap. If you’re new to the field and still unfamiliar with the command-line interface (CLI), you can try using this tool for a more user-friendly experience.
Ncat

Ncat, previously known as netcat, is a simple tool that allows you to view and record data on TCP or UDP network connections. It serves as a backend listener, enabling port scanning and port listening.
Ncat is commonly used for back-connecting or obtaining a reverse shell access to a target system. It provides a reliable and versatile means of establishing connections and exchanging data between systems. Its functionality makes it a valuable tool for various cybersecurity tasks, such as network troubleshooting, port forwarding, and remote administration.
Metasploit
Metasploit is not just a tool but a comprehensive framework that greatly aids in the pentesting process.
Metasploit contains a wide range of exploit modules and vulnerability scanners that have been discovered and published. With Metasploit, you can create payloads and send them to the target computer or server.
Within Metasploit, the module library is extensive, allowing you to perform tasks such as back-connecting and port scanning. Additionally, you can even add your own exploit modules to the Metasploit Framework, expanding its capabilities further. This versatility and extensibility make Metasploit a valuable asset for penetration testers, providing a powerful arsenal of tools for conducting security assessments and testing.
Nikto

Nikto is an open-source tool capable of performing scanning during web server pentesting. The scanning process includes identifying outdated software and configuration errors.
Nikto is also equipped with anti-IDS plugins, allowing you to perform stealthy scans that go undetected by firewalls that may be installed on the target web server. This feature enhances the effectiveness of the scanning process, ensuring that potential vulnerabilities are identified without raising alarms or triggering defensive mechanisms.
With its extensive database of known vulnerabilities and comprehensive scanning capabilities, Nikto is a valuable asset for conducting thorough security assessments of web servers and identifying potential weaknesses that could be exploited by attackers.
Burp Suite

Burp Suite is a favorite tool among web application pentesters. It provides a wide range of modules for scanning during the pentesting process.
This tool supports all stages of web server security testing, from scanning to exploitation. One of the key features of Burp Suite is its ability to intercept HTTP requests and modify them before they are sent back to the server. This allows you to observe and analyze any differences in the server’s response.
With its comprehensive set of features, Burp Suite enables testers to identify vulnerabilities, analyze web application behavior, and simulate various attack scenarios. It offers advanced options for manual testing, automated scanning, and reporting, making it an essential tool for effective web application penetration testing.
John the Ripper

Password cracking remains the de-facto authentication standard in many systems. Even after gaining access to a server or database, there are times when you need to crack passwords to obtain higher privileges within a system.
John the Ripper is a tool used for password cracking. It is popular because it supports custom wordlists and can be used to crack most popular hash algorithms such as MD5 and SHA.
With its powerful capabilities, John the Ripper assists in identifying weak passwords, testing password strength, and conducting password audits. It is a valuable tool for security professionals and penetration testers in assessing the security of systems and identifying potential vulnerabilities.
This concludes the list of essential tools that should be known and explored if you are interested in entering the field of cybersecurity. If you have any additional tools to suggest, please feel free to leave a comment.